Secure HPC
What is Secure HPC?
Secure HPC is an HPC tool designed to provide robust security for sensitive computational non-interactive batch jobs on shared HPC systems. It addresses the need for secure data processing in environments where traditional HPC systems, optimized for performance, lack adequate security measures to protect highly sensitive data. Secure HPC ensures data integrity and confidentiality, allowing researchers to transfer, store, and analyze sensitive information safely.
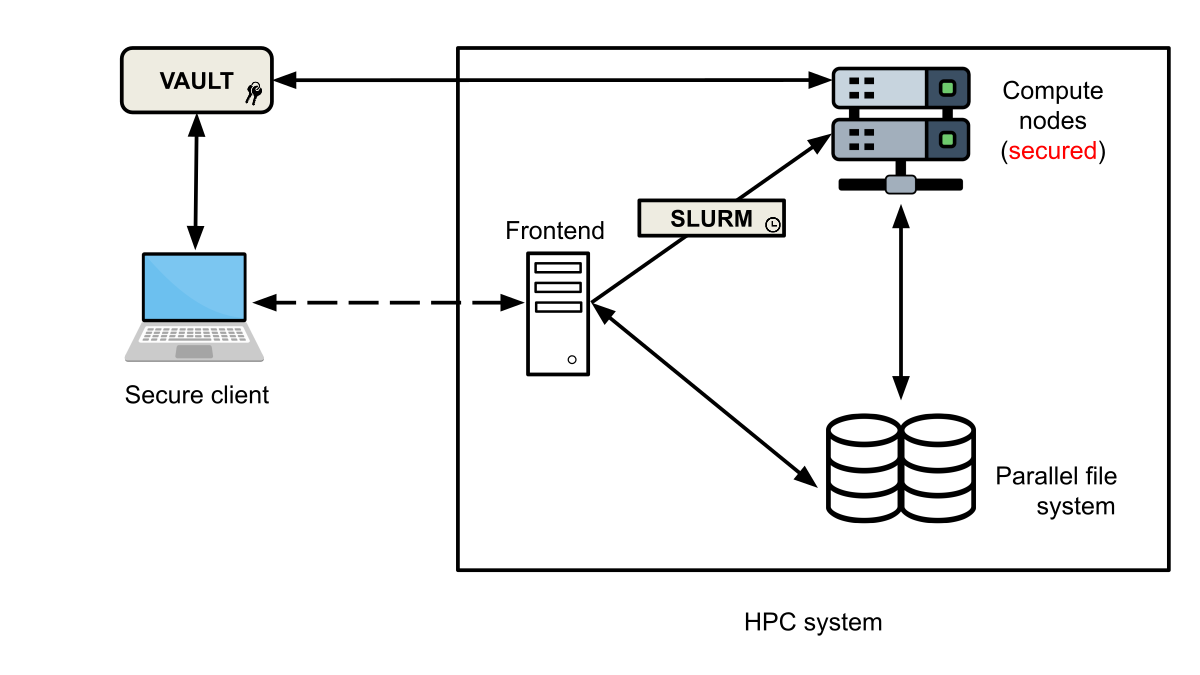
Secure HPC integrates several components, and a few of them are highlighted in the above image. Vault serves as a Key Management System (KMS) to securely store and share encryption keys between the HPC system and the secure client. The HPC frontend nodes are used by the secure client to submit encrypted batch jobs. Slurm, the resource manager, schedules and manages the encrypted jobs across the secured compute nodes. These compute nodes are isolated to prevent unauthorized access and ensure data integrity during processing. Additionally, the parallel file system offers high-speed storage while maintaining data encryption. The secure client is assumed to be a secure Linux machine and is used to interact with the Secure HPC environment, ensuring that data remains protected from the user’s side as well. Note that this excludes most public cloud machines, as they are not fit to handle unencrypted sensitive data. Together, these components create a secure environment that safeguards sensitive data throughout the computation lifecycle.
Purpose and Importance of Secure HPC
Secure HPC is designed to facilitate the secure processing of sensitive data on HPC systems. Its primary goals are to ensure data integrity, confidentiality, and compliance with data protection regulations such as GDPR while maintaining the high computational performance needed for scientific research.
Key Features
- End-to-End Data Encryption:
- Data is encrypted both at rest and in transit using advanced encryption techniques.
- Encrypted LUKS containers and Singularity/Apptainer containers ensure secure storage and computation.
- Role-Based Access Control:
- Secure HPC employs strict access control mechanisms to limit data access to authorized users only.
- Role-based permissions help manage user access efficiently.
- Secure Container Execution:
- Utilizes Singularity/Apptainer containers to isolate computational tasks, reducing the risk of unauthorized data access.
- Containers are encrypted and securely executed on HPC nodes.
- Key Management System (Vault):
- Integrated with Vault for secure key management, ensuring that encryption keys are stored and managed securely.
- Automated key retrieval and use during job execution.
- Zero-Trust Architecture:
- Each secure node has to authenticate with its own private key before being able to get the sensitive data.
- The secure client signs each job, ensuring that only authorized users are allowed to submit jobs.
- Since the batch script is fully encrypted, the content of the scripts cannot be seen from within SLURM.
- Automated Workflow:
- Secure workflow for data transfer, storage, and processing, minimizing manual intervention and reducing the risk of human error.
- Detailed step-by-step execution processes to guide users through secure job submission and data retrieval.
Benefits
- Enhanced Security:
- Protects sensitive data from unauthorized access and breaches, ensuring data integrity and confidentiality.
- Reduces the attack surface by minimizing the need for direct interaction with the host operating system.
- Regulatory Compliance:
- Helps researchers comply with data protection regulations, enabling them to securely process and share sensitive data.
- Ensures that sensitive data is handled according to legal and institutional requirements.
- Maintained Performance:
- Provides robust security without compromising the high performance of HPC systems.
- Efficient handling of encrypted data and containers to maintain computational speed and resource utilization.
- User Trust and Collaboration:
- Builds trust among researchers by ensuring that their data is secure, fostering collaboration and data sharing.
- Encourages the use of HPC resources for sensitive data processing across different scientific domains.
- Future-Proof Security:
- Adaptable to new security threats and vulnerabilities, providing a future-proof solution for secure data processing.
- Continuous updates and improvements to keep up with evolving cybersecurity challenges.
More Information
Secure HPC is based on A Secure Workflow for Shared HPC Systems (PDF), which details many of the underlying rationales and the details of the key exchange mechanisms.
- To understand whether Secure HPC fits your use case, see the Use Cases & Requirements Section.
- For a practical guide on how to set up a new Linux client to be able to submit Secure HPC jobs, see the Getting Started Guide.
- Lastly, to see what a successful Secure HPC project could look like, see the Success Stories